Background
After 18 months of remote academics and work, UW returns to campus operations in a hybrid environment. Members of the UW community have spent a year telecommuting to their respective areas on the UW network. The University will now resume operations with a hybrid model in which staff members have access at home and at work. The following is a write-up of observations and conclusions drawn from analyzing this problem set.
Problem
Full telework meant that data was for the most part stationary. Hybrid work calls for staff to conduct their work on-premise and at home, and this expands their threat surface significantly. Cyber attackers have not slowed down their targeting due to the pandemic. Incidents actually increased by 200% at the peak of the pandemic in 2020. Cyber attackers are likely to leverage “headline news” to target specific audiences.¹ Security researchers have also identified a 700% increase in IoT-specific malware, indicating the need to patch and update on-premise UW devices.²
Implications
Expanded Threat Surface
Before COVID, UW saw over 1 million unique devices on campus throughout the year. Post-COVID, this number hit just shy of 200k. The device count will not only return to normal, but it will likely increase as users will use devices they accumulated for distance learning and remote work. With this increase comes the concern of an expanded threat surface. Personal devices that have traditionally been kept off campus will now be brought on campus. While this is not new for campus WiFi and academic networks, it is new for some operational networks. Vulnerabilities and malware on personal devices may now access areas of the UW network they have not traditionally accessed. Unmanaged workstations issued by UW may also host these same threats if not properly configured and patched.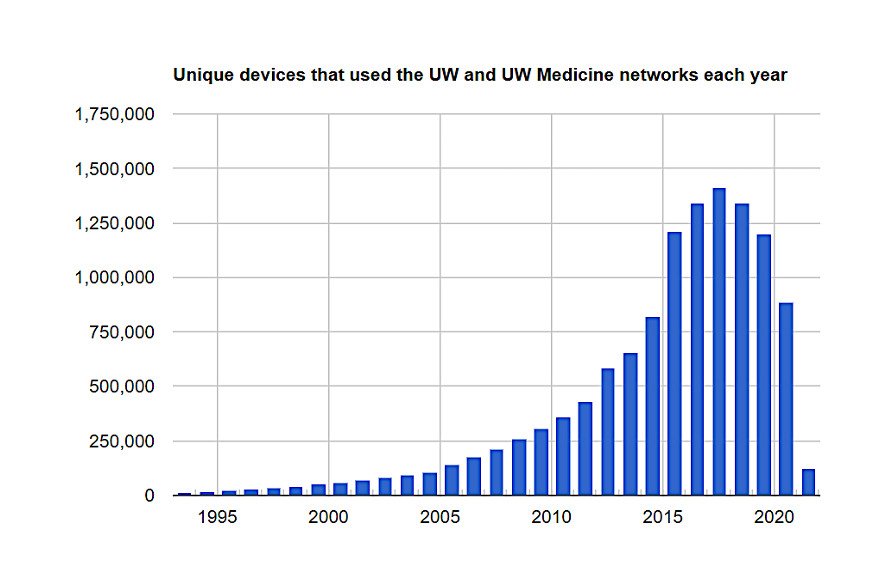
Personal device usage to access private areas on the UW network has traditionally entailed the use of a VPN. In order to understand this usage, the Office of Information Security conducted a poll during the August 2021 information security briefing. A group of 20 UW professionals were asked about full and split-tunnel usage at UW. Over 50% stated they utilized split-tunnel VPN. This coincides with historical data indicating nearly 70% of campus VPN connections were on the Husky OnNet split tunnel.
Split-tunnel usage is cost-effective and causes less strain on UW resources, but it can give users a false sense of security. Full-tunnel usage provides protection through UW’s services such as the intrusion prevention system (IPS) and DNS monitoring. Split-tunnel usage only provides this security to campus connections. While using the split-tunnel VPN, connections to malicious downloads, spoofed sites, and from phishing emails can occur without any intervention from UW services. A compromised device can then utilize the VPN connection to communicate with internal assets and export over public internet.
As noted by information security specialists at Indiana University³, personal devices can still be infected while on a VPN. Individuals using their personal devices could be infected during off-work hours and bring that infection the next time they connect with the VPN. VPN usage is not the final answer, but it is a key layer in defending UW information assets.
Well-Crafted Phishing Campaigns
Security researchers at F5 reported that phishing incidents increased by 15% in 2020 compared to the previous year, with a 220% increase in phishing incidents during the lockdown month of March.¹ Many of these messages capitalize on the fear set in by the pandemic with messages such as “COVID relief” and “economic relief information.” The Office of Information Security continually monitors reported phishing emails and has observed similar dialogue directed towards members of the UW community.
University staff will likely receive phishing emails specifically crafted for the return-to-work scenario. Furthermore, with prevalent news messages of vaccine attestation and exemptions, cyber attackers will capitalize on the advertised deadlines to target victims.
IoT Patching and Updating
In a UW poll conducted in August 2021, a sample group of 32 UW employees were asked “What is the biggest threat to UW’s information security with a hybrid return to work?”
The most common responses were:
- Unpatched devices
- Malware
- Missing software updates
This same poll was given to a group of 8 information security professionals and resulted in similar responses with patching and malware being a top area of concern.
With many IoT devices, computer labs, and on-premise systems not being used over the past year, many unrealized patches and updates may surface. Utilization of these devices without their updates pose a serious security concern as they are vulnerable to infection that could be used as a staging ground for more serious attacks.
Things to Do
The Office of Information Security recommends the following in order to combat these key issues:
UW Network Users
- 60% of data breaches originate from employees/insiders. Understand that you, the user, are the target of cyber attackers.
- Keep sensitive UW information on UW devices. Do not aggregate sensitive files on your personal device, not even in your downloads folder.
- Refresh your remote work habits by watching the Working Remotely online training.
- Fortify your personal device by reading the Securing Laptops Risk Advisory.
System Administrators/Owners
- Patch and/or upgrade assets.
- Limit IoT usage within secured network areas, especially network attached storage devices.
- Implement access of least privilege. As people return to campus, it’s a great time to audit access.
- Review the NSA’s advisory for securing devices in public settings.
Organizational Leaders
- Re-communicate APS 55.1, Mobile Device Use and Allowance Policy to staff members.
- Work with administrators and users for a “cyber check-up” as devices return to the network.
- Communicate full-tunnel and split-tunnel connection requirements.
- Indiana Universities approach: “Utilize the VPN for connections that could not occur outside of the university.”³
- Encourage full-tunnel VPN connections when explicitly working with critical and sensitive UW information assets.
- For more information, review the Husky OnNet documentation on IT Connect.
References
- F5: 2020 Phishing and Fraud Report
- Threat Labz: IoT in the Enterprise: Empty Office Edition
- Business Horizons: Balancing risk with virtual private networking during a pandemic